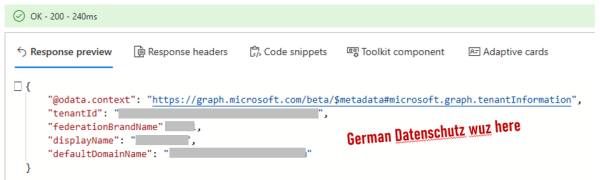
When you open a Microsoft Form asking you for some sensitive data, do you know where will your data land? Could it be phishing? Read on to find out... Recently, I have received an email at work asking me to fill out a form with some of sensitive personal details (voluntary disclosure). I don't mind... Continue Reading →
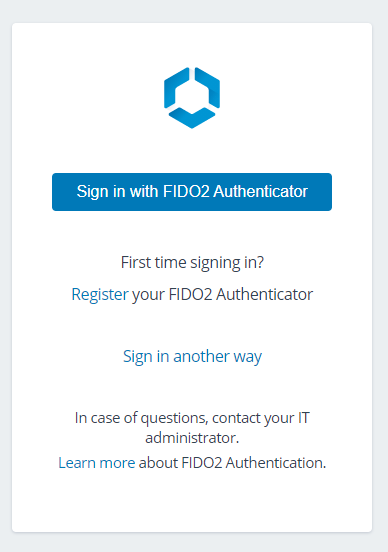
Adding FIDO2 + Windows Hello fingerprint auth to Workspace ONE
This will be a short "recipe" type of post on how to showcase a new feature that was introduced in latest Workspace ONE Access SaaS release (sorry, no news for on prem now): FIDO2 auth. The video shows Yubikey, which I don't have, so I will be using Windows Hello (which in turn will use... Continue Reading →
Android 11 COPE and the end of Internal apps
We know about the changes to Android 11 COPE, and how they affect the EMMs. One aspect that was slightly overlooked though, is what happens to Internal apps, which many organizations are still employing. We have recently released a KB, which caused a bit of panic between customers and colleagues. Let’s dive deeper and see... Continue Reading →
Android management in China – what are your options?
After I published the article regarding the enrollment of Android devices in closed networks, the hottest question was how to apply it for China. The answer is as usual “it depends”. If you want to know more – read on! What’s the problem?What options are available?What is the optimal approach? What’s the problem? Problem is... Continue Reading →
Watch your certificates when working with Apple devices!
A while ago a colleague turned to me for help. Customer tested iOS, Android and Win10 with a SCEP server. Win10 and Android had no issues, but on iOS the certificates failed to install with a cryptic error. I decided to write a blog about it, because I expect a second wave of such issues... Continue Reading →
Zoom vs Teams – security options
Zoom banned? Think Teams is better? Show this to your boss.
Remediate the Pixel4 and Galaxy S10 biometric security flaws with Workspace ONE
I am pretty sure you've heard already about the issues with Samsung Galaxy S10 fingerprint sensor and Google Pixel 4 Face Unlock. Both companies have acknowledged the issues and committed to releasing the patches "soon" (Samsung is said to be testing fixes in certain countries already). What can you in the meantime? With Workspace ONE... Continue Reading →
Hidden TCPdump and ETHtool on VMware UAG
VMware UAG (Unified Access Gateway) is a cool little security appliance, deployable on vSphere, AWS, Azure etc that hosts a lot of Workspace ONE edge services: Horizon Proxy, Web Reverse Proxy, Tunnel VPN Gateway, Content Gateway and (since 3.6) the Secure Email Gateway. The challenge is that the thing was built to be headless and... Continue Reading →
On Apple, Security by Obscurity and WS1 Trust Network.
In the last several weeks a number of bugs were found in Apple's iOS, MacOS and protocols. This had coincided with a partner workshop last Friday, where the decisive argument was "Have you ever heard of an Antivirus for an iPhone". Here's what came out.
Apple iOS User Enrollment vs Android Enterprise and the real MDM needs #WWDC2019
Every WWDC has a session called What’s New in Managing Apple Devices. This year's one was no exception. During this session Apple presented they new take on BYOD called User Enrollment. Here's my brief analysis and comparison with Android Enterprise. Links to the source video, slide deck and some other useful resources are below. TL:DR... Continue Reading →