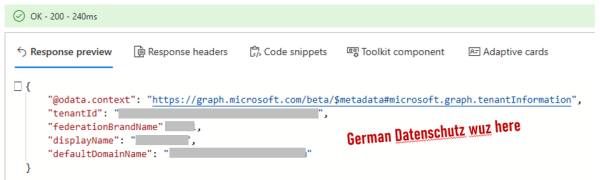
When you open a Microsoft Form asking you for some sensitive data, do you know where will your data land? Could it be phishing? Read on to find out... Recently, I have received an email at work asking me to fill out a form with some of sensitive personal details (voluntary disclosure). I don't mind... Continue Reading →
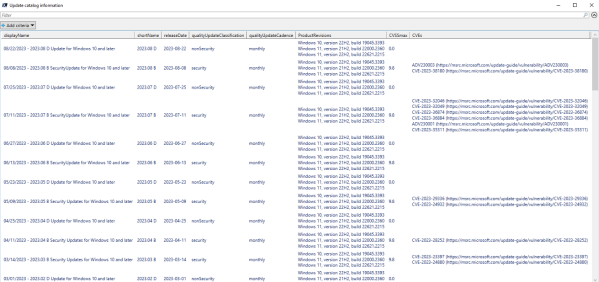
Enhancing Windows Update Catalog metadata Accessibility
Microsoft has recently released a major update to the Windows Update catalog back-end, adding crucial information such as CVEs (Common Vulnerabilities and Exposures) addressed by the update and the CVE Score directly info API. This information is essential for Threat and Vulnerability Management decisions as well as Patch management and many organizations pay $$ for... Continue Reading →
Quickly validate and enable manual application uninstall via Intune Company Portal using Graph API
I am back and the titles are getting longer! If you are an Intune admin, you will probably be happy to know that one of the most required features has landed: Uninstall Win32 and Microsoft store apps using the Windows Company Portal. One thing you need to be aware of, is that this feature is... Continue Reading →
Building a custom Windows Update Report p1: Parsing HTML via PowerShell on modern systems (no IE)
Wow, it's been a while! A customer of mine recently wanted a detailed report that should include info such as how many weeks is the Windows on the machine behind the latest available Security Update. We've found to a way to combine Intune Data Warehouse and PowerBI to pull data that allows to identify the... Continue Reading →
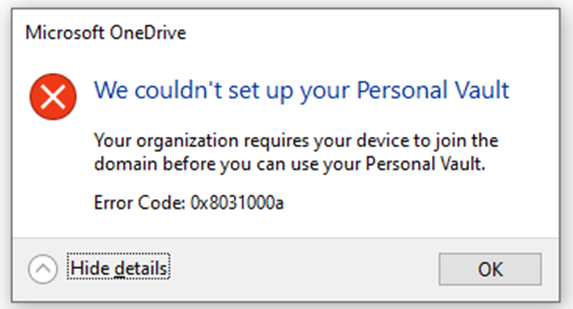
A case of OneDrive Personal Vault not coming up (0x8031000a, MDM, GPO and BitLocker)
Today I wanted to enable the Personal Vault feature on my Home PC. While following the wizard I got an error 0x8031000a "Your organization requires your device to join the domain before you can use the Personal Vault". What does this have to do with MDM. GPO and BitLocker troubleshooting? Here's some quick Friday entertainment!... Continue Reading →
Clean up references to your custom domain name from an Azure AD test tenant
Today I needed to move my custom domain name from an old (and messy) AAD test tenant to a (sparkling) new one. Problem is, you can't simply delete the old custom name, since your user's UPNs and Email addresses are using it (AAD actually presents a nice screen, showing all the dependencies, but I am... Continue Reading →
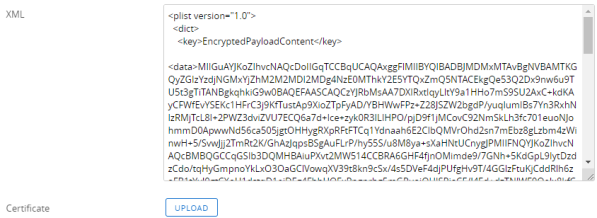
Viewing the encrypted Apple profiles in Workspace ONE UEM console
Apple has an option to encrypt the MDM profile payloads (both iOS and macOS). But then when you try to view the profile XML in the console (ex. migrating payloads between UAT and Production environments, working with custom profiles) - they are encrypted! Turns out, there is a way to view the XML w/o having... Continue Reading →
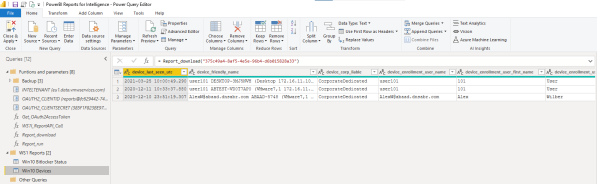
Integrating Workspace ONE reporting with PowerBI
Last week one of my customers asked if Workspace ONE data could be used in PowerBI. Since Workspace ONE Intelligence Reports are included in every WS1 edition and are accessible via API - this is the easiest way to expose data to external systems. But how exactly? Even though I've never used PowerBI before, after... Continue Reading →
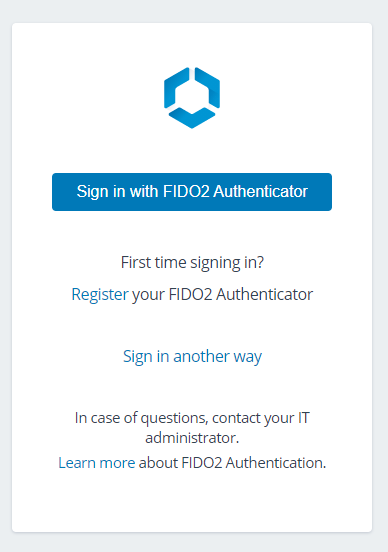
Adding FIDO2 + Windows Hello fingerprint auth to Workspace ONE
This will be a short "recipe" type of post on how to showcase a new feature that was introduced in latest Workspace ONE Access SaaS release (sorry, no news for on prem now): FIDO2 auth. The video shows Yubikey, which I don't have, so I will be using Windows Hello (which in turn will use... Continue Reading →
App version management in Android Enterprise – Managed Play Closed Tracks and their nuances
If you think my titles are wordy, check the official title of good old Robinson Crusoe! Anyway, today we will look at two important things: Using Managed Google Play feature called Closed Tracks to control app versions and update cycles in two scenarios:Multiple "deployment rings" for different device groupsDeveloper having customers with different update cyclesImportant... Continue Reading →